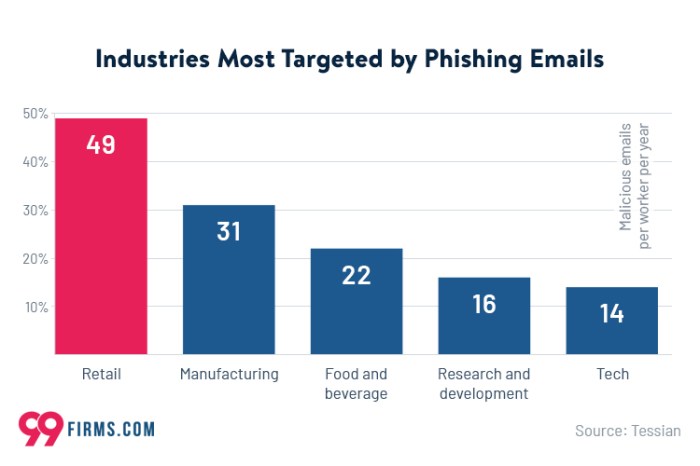
Phishing is responsible for most of the recent PII breaches, posing a significant threat to individuals and organizations alike. This nefarious practice targets sensitive information, leaving victims vulnerable to identity theft, financial loss, and emotional distress.
Phishing attacks employ various methods, including spoofed emails, malicious websites, and social engineering tactics. These techniques are designed to deceive victims into revealing their personal data, often with devastating consequences.
Phishing as a Leading Cause of PII Breaches: Phishing Is Responsible For Most Of The Recent Pii
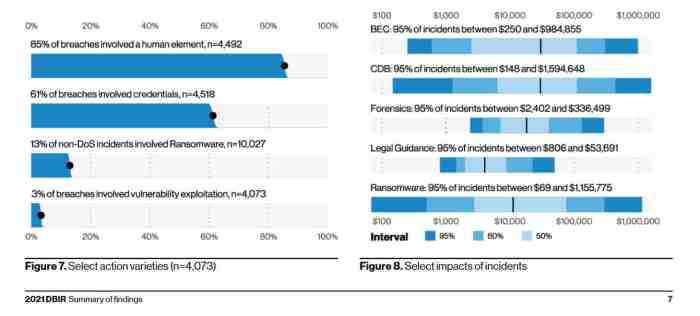
Phishing attacks have emerged as a significant threat to personal identifiable information (PII) security, accounting for a substantial portion of recent data breaches. Statistics from various organizations, including the Federal Bureau of Investigation (FBI) and Verizon’s Data Breach Investigations Report, indicate that phishing is responsible for a majority of PII breaches.
Phishing attacks target individuals and organizations through deceptive emails, malicious websites, and social engineering tactics. These attacks aim to trick victims into revealing their sensitive information, such as passwords, credit card numbers, and social security numbers.
Methods Used in Phishing Attacks
- Spoofed Emails:Attackers create emails that appear to originate from legitimate organizations or individuals to trick victims into clicking on malicious links or attachments.
- Malicious Websites:Attackers create fake websites that mimic legitimate ones to lure victims into entering their PII. These websites may appear identical to the original, making it difficult for victims to detect the deception.
- Social Engineering Tactics:Attackers use psychological manipulation to convince victims to divulge their PII. This may involve posing as customer support representatives or using fear and urgency to pressure victims into taking immediate action.
Impact of Phishing on Individuals and Organizations
Phishing attacks have severe consequences for both individuals and organizations.
Individuals:
- Identity Theft:Phishing attacks can lead to identity theft, where attackers use stolen PII to create fraudulent accounts or access existing ones.
- Financial Loss:Victims may experience financial losses due to unauthorized purchases, fraudulent transactions, or theft of sensitive financial information.
- Emotional Distress:Phishing attacks can cause emotional distress, anxiety, and reputational damage to victims.
Organizations:
- Reputational Damage:Phishing breaches can damage an organization’s reputation and erode customer trust.
- Financial Losses:Organizations may incur financial losses due to legal liabilities, fines, and recovery costs associated with data breaches.
- Operational Disruptions:Phishing attacks can disrupt an organization’s operations, leading to downtime and loss of productivity.
Prevention and Mitigation Strategies, Phishing is responsible for most of the recent pii
To protect against phishing attacks, individuals and organizations can implement the following strategies:
Individuals:
- Recognize Suspicious Emails and Websites:Be cautious of emails and websites that appear suspicious, such as those with grammatical errors, unfamiliar sender addresses, or requests for personal information.
- Use Strong Passwords and Two-Factor Authentication:Use strong passwords and enable two-factor authentication to protect online accounts.
- Be Aware of Social Engineering Tactics:Be aware of common social engineering tactics and never share personal information over email or phone unless you are certain of the recipient’s identity.
Organizations:
- Employee Training and Awareness Programs:Train employees on phishing risks and best practices to identify and avoid phishing attacks.
- Security Awareness Campaigns:Conduct regular security awareness campaigns to educate employees about the latest phishing threats.
- Technological Solutions:Implement technological solutions, such as email filtering systems, anti-phishing software, and intrusion detection systems, to detect and block phishing attacks.
Helpful Answers
What are the common methods used in phishing attacks?
Phishing attacks typically involve spoofed emails, malicious websites, and social engineering tactics, which trick victims into revealing their personal information.
What are the consequences of phishing attacks?
Phishing attacks can lead to identity theft, financial loss, emotional distress, and reputational damage for organizations.
How can individuals protect themselves from phishing?
Individuals should be cautious when interacting with emails and websites, use strong passwords, and enable two-factor authentication to protect themselves from phishing attacks.